Residential proxies

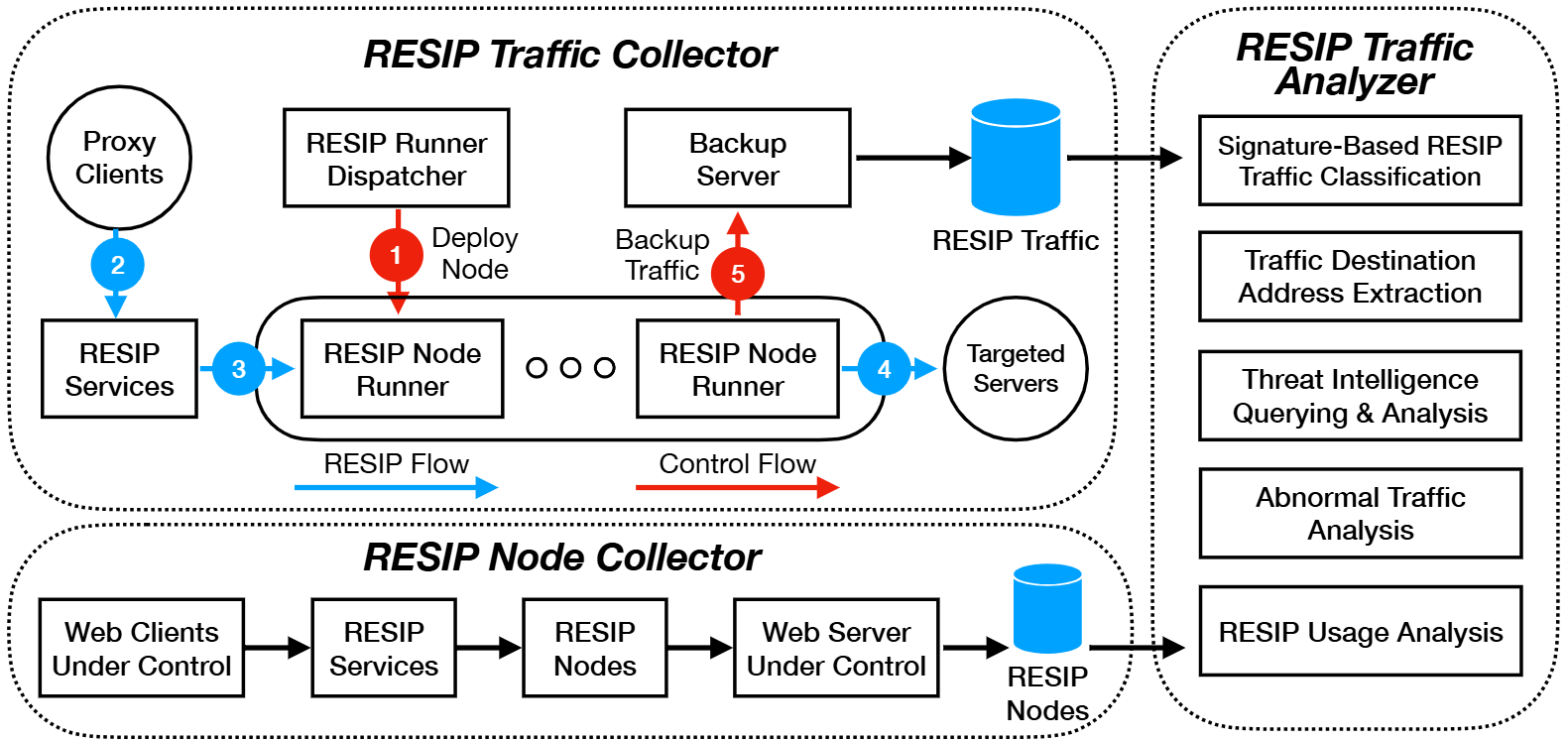
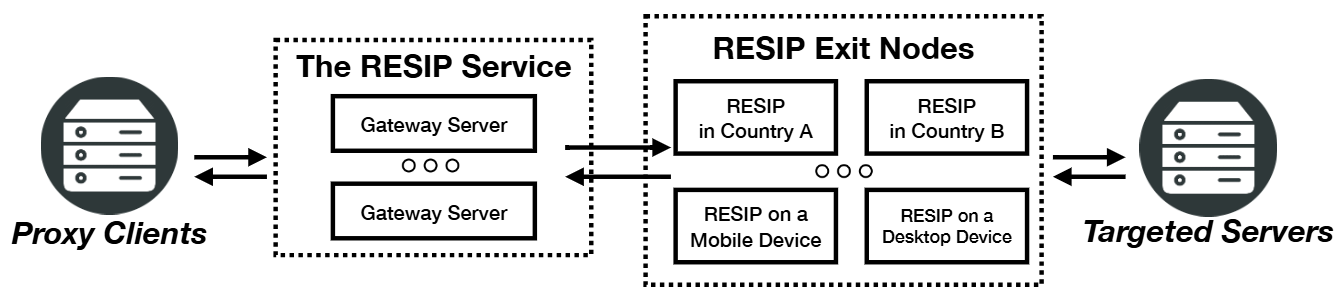
Residential proxies (RESIP) are web proxies located in either residential or cellular networks. As illustrated in Figure, a typical RESIP works in a backconnect mode wherein proxy traffic sourced from a proxy customer will be first sent to the gateway server, which in turn forwards the traffic to a RESIP node, before exiting to the traffic destination. What's more, most RESIP services will allow proxy customers to specify where they want to exit the relayed traffic, in terms of countries and cities. Also, proxy customers are able to stick their traffic to the same exit node, either through passing the same session id or connecting to some sticky proxy gateways which usually bind to an exit node for every 5 or 10 minutes.